| 网站 | 直连 | 说明 |
|---|---|---|
| https://android-apk.app/ | 否 | 可搜索,可下载历史版本 |
| https://apkpure.com/cn/ | 否 | 可搜索,可下载历史版本 |
| https://apkcombo.com/apk-downloader/ | 否 | 可搜索,可下载历史版本 |
| https://androidappsapk.co/ | 否 | 可搜索,可下载历史版本 |
| https://apk.support/apk-downloader | 否 | 需要自己输入应用地址,解析的是Google下载地址 |
| https://apps.evozi.com/apk-downloader/ | 否 | 需要自己输入应用地址 |
| https://apkhome.net/ | 是 | 可搜索,但版本不一,有的APK文件十分可疑 |
| https://www.apkmirror.com/ | 否 | 可搜索,可下载历史版本 |
| https://androidapksfree.com | 否 | 可搜索,可下载历史版本 |
| https://www.apkhere.com/ | 否 | 不是很全,有很多破解的APP |
| https://www.apk4fun.com/ | 否 | |
| https://www.aptoide.com/ | 否 | |
| https://www.apkmonk.com/ | 否 | |
| https://cn.uptodown.com/android | 否 | |
| https://www.9apps.com/ | 否 | |
| https://download.cnet.com/android/ | 否 | |
| https://apkmos.com/ | 是 | 不全 |
分类目录归档:应用安全
编译Metasploit安卓Payload时报错解决笔记
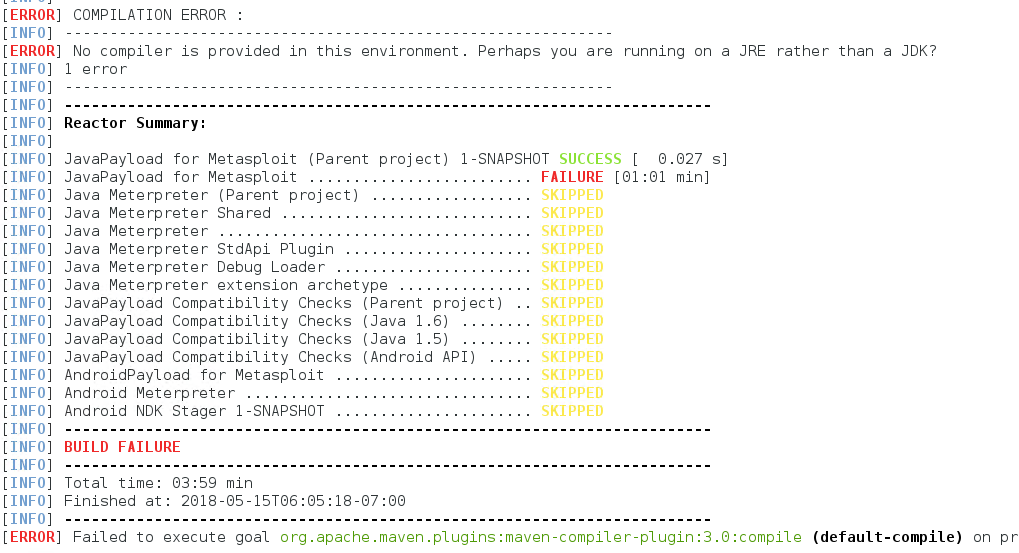
在编译Metasploit的安卓payload时,报出以下错误
[ERROR] COMPILATION ERROR :
[INFO] ————————————————————-
[ERROR] No compiler is provided in this environment. Perhaps you are running on a JRE rather than a JDK?
[INFO] 1 error
报错后,所有编译处在SKIPPED状态,如下图:
两款Android远控(DroidJack+SpyNote)使用记录
第一款:DroidJack
功能介绍:
1、可以生成一个APK,绑定在被控手机的任何APP上
2、可在电脑端控制手机,包括浏览、传输、删除文件等
3、可进行SMS短信收发和查看功能
4、可以控制手机的电话功能
5、联系人管理
6、麦克风监听
7、GPS定位
8、APP管理
修改Metasploit安卓Payload源码以实现持久化访问
Metasploit-Payload是广泛使用的安卓后门之一,然而无论是直接使用msfvenom生成的apk文件,还是通过其他手段将payload注入到已有apk中,其连接稳定性都非常差,基本在APP启动的一刹那可以建立连接,如果网络不稳定,中断后不会再次连接。本文将通过直接修改安卓payload源码已实现持久化访问。
代码审计工具列表
代码审计工具收集
| Tool | Language(s) | Avail. | CCR | Finds or Checks for | as of |
| ABASH | Bash | free | String expansion errors, option insertion errors, and other weaknesses that may lead to security vulnerabilities. | Mar-12 | |
| ApexSec Security Console | PL/SQL(Oracle Apex) | Recx | SQL Injection, Cross-Site Scripting, Access Control and Configuration issues within an Apex application | Mar-10 | |
| Astrée | C | AbsInt | undefined code constructs and run-time errors, e.g., out-of-bounds array indexing or arithmetic overflow. | Jun-09 | |
| BOON | C | free | integer range analysis determines if an array can be indexed outside its bounds | Feb-05 | |
| bugScout | Java, C#, Visual Basic, ASP, php | buguroo | multiple security failures, such as deprecated libraries errors, vulnerable functions, sensitive information within the source code comments, etc. | Mar-12 | |
| C/C++test® | C, C++ | Parasoft | defects such as memory leaks, buffer issues, security issues and arithmetic issues, plus SQL injection, cross-site scripting, exposure of sensitive data and other potential issues | Dec-13 | |
| dotTEST™ | C#, VB.NET, MC++ | ||||
| Jtest® | Java | ||||
| HP Code Advisor (cadvise) | C, C++ | HP | many lint-like checks plus memory leak, potential null pointer dereference, tainted data for file paths, and many others | Dec-13 | |
| Checkmarx CxSAST | Java, JavaScript, PHP, C#, VB.NET, VB6, ASP.NET, C/C++, Apex, Ruby, Perl, Objective-C, Python, Groovy, HTML5, Swift, APEX, J2SE, J2EE | Checkmarx | All OWASP Top 10 and SANS 25 vulnerabilities and compliance with PCI-DSS, HIPAA, and MISRA requirements along with custom queries, all with a low rate of false-positives and easy to integrate throughout the SDLC. | Mar-16 | |
| Clang Static Analyzer | C, Objective-C | free | Resports dead stores, memory leaks, null pointer deref, and more. Uses source annotations like “nonnull”. | Aug-10 | |
| Closure Compiler | JavaScript | free | Removes dead code, checks syntax, variable references and types and warns about common JavaScript pitfalls. | Feb-14 | |
| CodeCenter | C | ICS | incorrect pointer values, illegal array indices, bad function arguments, type mismatches, and uninitialized variables | Apr-11 | |
| CodePeer | Ada | AdaCore | detects uninitialized data, pointer misuse, buffer overflow, numeric overflow, division by zero, dead code, concurrency faults (race conditions), unused variables, etc. | Apr-10 | |
| CodeSecure | ASP.NET, C#, PHP, Java, JSP, VB.NET, others | Armorize Technologies | XSS, SQL Injection, Command Injection, tainted data flow, etc. | Aug-12 | |
| CodeSonar | C and C++ | GrammaTech | null-pointer dereferences, divide-by-zeros, buffer over- and underruns | Nov-12 | |
| Coverity SAVE™ | C, C++, Java, C# | Coverity | flaws and security vulnerabilities – reduces false positives while minimizing the likelihood of false negatives. | Apr-11 | |
| Cppcheck | C, C++ | free | pointer to a variable that goes out of scope, bounds, classes (missing constructors, unused private functions, etc.), exception safety, memory leaks, invalid STL usage, overlapping data in sprintf, division by zero, null pointer dereference, unused struct member, passing parameter by value, etc. Aims for no false positives. | Feb-10 | |
| CQual | C | free | uses type qualifiers to perform a taint analysis, which detects format string vulnerabilities | Feb-05 | |
| Csur | C | free | cryptographic protocol-related vulnerabilities | Apr-06 | |
| DoubleCheck | C, C++ | Green Hills Software | like buffer overflows, resource leaks, invalid pointer references, and violations of … MISRA | Jul-07 | |
| FindBugs | Java, Groovy, Scala | free | Null pointer deferences, synchronization errors, vulnerabilities to malicious code, etc. It can be used to analyse any JVM languages. | Sep-12 | |
| FindSecurityBugs | Java, Groovy, Scala | free | Extends FindBugs with more security detectors (Command Injection, XPath Injection, SQL/HQL Injection, Cryptography weakness and many more). | Jun-16 | |
| Flawfinder | C/C++ | free | uses of risky functions, buffer overflow (strcpy()), format string ([v][f]printf()), race conditions (access(), chown(), and mktemp()), shell metacharacters (exec()), and poor random numbers (random()). | 2005 | |
| Fluid | Java | call | “analysis based verification” for attributes such as race conditions, thread policy, and object access with no false negatives | Oct-05 | |
| Goanna Studio and Goanna Central | C, C++ | Red Lizard Software | memory corruptions, resource leaks, buffer overruns, null pointer dereferences, C++ hazards, MISRA C 2012, … | Mar-15 | |
| HP QAInspect | C#, Visual Basic, JavaScript, VB Script | Fortify | application vulnerabilities | Apr-11 | |
| Insight | C, C++, Java, and C# | Klocwork | Buffer overflow, un-validated user input, SQL injection, path injection, file injection, cross-site scripting, information leakage, weak encryption and vulnerable coding practices, as well as quality, reliability and maintainability issues. | May-11 | |
| Jlint | Java | free | bugs, inconsistencies, and synchronization problems | Aug-12 | |
| LAPSE | Java | free | helps audit Java J2EE applications for common types of security vulnerabilities found in Web applications. | Sep-06 | |
| ObjectCenter | C/C++ | ICS | “run-time and static error detection … more than 250 types of errors, including more than 80 run-time errors … inter-module inconsistencies” | Apr-11 | |
| Parfait | C/C++ ? | Oracle proprietary | Apr-13 | ||
| PLSQLScanner 2008 | PLSQL | Red-Database-Security | SQL Injection, hardcoded passwords, Cross-site scripting (XSS), etc. | Jun-08 | |
| PHP-Sat | PHP | free | static analysis tool, XSS, etc. description | Sep-06 | |
| Pixy | PHP | free | static analysis tool, only detect XSS and SQL Injection. No home page? | Jun-14 | |
| PMD | Java | free | questionable constructs, dead code, duplicate code | Feb-06 | |
| PolySpace | Ada, C, C++ | MathWorks | run-time errors, unreachable code | Sep-13 | |
| PREfix and PREfast | C, C++ | Microsoft proprietary | Feb-06 | ||
| pylint | Python | free | Checks for errors and looks for bad code smells. | Feb-14 | |
| QA-C, QA-C++, QA-J | C, C++, Java | Programming Research | A suite of static analysis tools, with over 1400 messages. Detects a variety of problems from undefined language features to redundant or unreachable code. | May-09 | |
| Qualitychecker | VB6, Java, C# | Qualitychecker | static analysis tool | Sep-07 | |
| Rational AppScan Source Edition | C, C++, Java, JSP, ASP.NET, VB.NET, C# | IBM (formerly Ounce Labs) | coding errors, security vulnerabilities, design flaws, policy violations and offers remediation | Aug-10 | |
| RATS (Rough Auditing Tool for Security) | C, C++, Perl, PHP, Python | free | potential security risks | Sep-13 | |
| Resource Standard Metrics(RSM) | C, C++, C#, and Java | M Squared Technologies | Scan for 50 readability or portability problems or questionable constructs, e.g. different number of “new” and “delete” key words or an assignment operator (=) in a conditional (if). | Apr-11 | |
| RIPS | PHP | free and RIPS Tech | all types of injection vulnerabilities, including PHP-specific and second-order vulnerabilities | May-16 | |
| Smatch | C | free | simple scripts look for problems in simplified representation of code. primarily for Linux kernel code | Apr-06 | |
| SCA | ASP.NET, C, C++, C# and other .NET languages, COBOL, Java, JavaScript/AJAX, JSP, PHP, PL/SQL, Python, T-SQL, XML, and others | Fortify Software | security vulnerabilities, tainted data flow, etc. “more than 470 types of software security vulnerabilities” | Aug-12 | |
| SPARK tool set | SPARK (Ada subset) | Altran | ambiguous constructs, data- and information-flow errors, any property expressible in first-order logic (Examiner, Simplifier, and SPADE) | Aug-06 | |
| SPARROW | C/C++, Java, JSP, JavaScript, C#, ASP(.NET), Objective-C, PHP, VB.NET, VBScript, HTML, SQL, XML | Fasoo | OWASP Top 10, SANS 25, CWE, CERT vulnerabilities, MISRA, efficient and effective issue management based on machine learning technology | Aug-16 | |
| Splint | C | free | security vulnerabilities and coding mistakes. with annotations, it performs stronger checks | 2005 | |
| TBmisra®, TBsecure® | C, C++, Java, Ada, Assembler | LDRA | The TBsecure module for LDRA Testbed® comes with the Carnegie Mellon Software Engineering Institute (SEI) CERT C secure coding standard. TBsecure identifies concerns such as buffer overflow, out-of-bounds array access, dangling pointers, double-free, and dereferencing null pointer. Other modules handle High Intergrity C++, HIS, IPA/SEC C, JSF++ AV, MISRA C/C++, and Netrino C. | 2013 | |
| UNO | C | free | uninitialized variables, null-pointers, and out-of-bounds array indexing and “allows for the specification and checking of a broad range of user-defined properties”. aims for a very low false alarm rate. | Oct-07 | |
| PVS-Studio | C++ | OOO “Program Verification Systems” (Co LTD) | PVS-Studio is a static analyer that detects errors in source code of C/C++/C++0x applitations. There are 3 sets of rules included in PVS-Studio: (1) Diagnosis of 64-bit errors (Viva64) (2) Diagnosis of parallel errors (VivaMP) (3) General-purpose diagnosis | Jan-10 | |
| xg++ | C | unk | kernel and device driver vulnerabilities in Linux and OpenBSD through range checking, etc. | Feb-05 | |
| Yasca | Java, C/C++, JavaScript, ASP, ColdFusion, PHP, COBOL, .NET, etc. | free | a “glorified grep” and aggregator of other tools, including: FindBugs, PMD, JLint, JavaScript Lint, PHPLint, CppCheck, ClamAV, RATS, and Pixy. “It is designed to be very flexible and easy to extend. … writing a new rule is as easy as coming up with a regular expression” | Mar-10 | |
| WAP | PHP | free | Finds or checks for: SQL Injection (SQLI) / Cross-site scripting (XSS) / Remote File Inclusion (RFI) / Local File Inclusion (LFI) / Directory Traversal or Path Traversal (DT/PT) / Source Code Disclosure (SCD) / OS Command Injection (OSCI) / PHP Code Injection |
如何学习逆向分析-老工程师的经验
一直想学习逆向分析,先攒点资料吧
摘自:http://www.freebuf.com/articles/system/119374.html
从事搬砖(逆向分析)这行也有好多年了,期间分析各种不同类型的样本,从最开始的window时代的鬼影第三代到第六代,蠕虫病毒,输入法,感染型,灰鸽子远程,熊猫烧香,游戏盗号,QQ盗号等样本,到后面Android时代的各种截持短信,流氓推广,弹广告,刷流量,刷ROM,以及后面手机端蠕虫,敲诈者,百脑虫,FakeDebugger,GhostPush,ios/mac上WireLurker,XcodeGhost,YiSpecter,ZergHelper,BackStab,KeyRaider,TinyV的等样本,以及现在linux上的一些恶意样本等,做为一名从业人员,有些是公司要求分析的,有些是自己觉得好玩下载分析的,我简单说说一些学习技巧与方法,需要的知识点,以及分析的大致流程。
(1)拿到一个样本,不管是什么,先弄清它是什么文件格式,这里就要求你要对不同的文件格式有所了解了:window(PE),linux(ELF),android(dex,ELF),ios/mac(mach-o)
(2)然后看样本有没有壳或加密,如果有壳就脱壳,有加密就看能不能解密
(3)脱完壳,解完密,后面就是动+静态分析了
动态调试:window(od,windbg),linux(gdb,edb),android(jeb,ida),ios/mac(lldb)
静态调试: ida,010Editor,readelf,objdump,string等
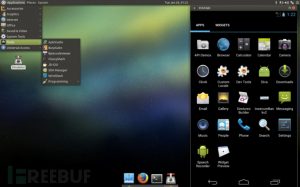
使用Androl4b进行安卓APP安全测试(Part 1)
文章转载自FreeBuf,拿来做下笔记。希望FB打造有态度的安全平台,为广大安全爱好者提供一个良好的技术交流空间。另:至刚易折,期待乌云回归。
0×00 前言
移动客户端Ap测试中,相信有很多小伙伴都是在自己常用的手机中安装上需要测试的App。这种方法是比较常见的一种,但是常用的手机中难免会有其它不相关的App在后台运行、进行网络请求,导致我们拦截到很多测试中不需要要的数据包甚至有的情况下我们无法辨别数据包是否是需要测试的App发出的请求。介于这种情况我们需要一个更干净的测试环境来对移动端App进行测试。
0×01工欲善其事必先利其器
Androl4b是一个基于ubuntu mate的安卓安全评估&测试的系统,系统集成了一系列Android 应用程序评估测试所需的工具,可用于逆向工程和恶意软件分析,为安卓测试、安全研究从业人员节省了大量环境搭建配置所需的时间、精力。
Androl4b,安卓安全评估测试利器
在Freebuf上看到了几篇关于APP测试的文章,正巧最近用的上,无耻的粘过来做个记录,后期慢慢整理。
Androl4b是一个基于ubuntu mate的安卓安全评估&测试的系统,系统集成了安全爱好者、安全研究员对于逆向工程以及恶意软件分析所需的工具,下面就让小编简单介绍下吧!
用户名:andro
密码:androlab
工具简介:
APKStudio :基于逆向工程IDE的跨平台QT5 安卓应用程序
ByteCodeViewer:安卓的apk逆向工程套装:反编译,编辑器,调试。
Lobotomy:安卓的逆向工程框架以及工具包(静态动态分析)
MobileSecurityFramework-MobSF:android/ iOS 自动化渗透测试框架(静态分析)
DroidBox:安卓应用程序动态分析
Dorzer:安卓应用程序安全评估框架
APKtool:apk逆向工具
AndroidStudio:安卓应用开发的IDE
ClassShark:安卓浏览器
BurpSuite:应用安全评估
Wireshark:网络协议分析